Introduction
Today we will be walking through one of the Blue Team Labs Online Investigations: Countdown. The Investigation is rated as "Medium" and will earn you 50 points. To earn full points, you have to answer 7 questions in regard to the following scenario:
NYC Police received information that a gang of attackers has entered the city and are planning to detonate an explosive device. Law enforcement have begun investigating all leads to determine whether this is true or a hoax.
Persons of interest were taken into custody, and one additional suspect named 'Zerry' was detained while officers raided his house. During the search they found one laptop, collected the digital evidence, and sent it to NYC digital forensics division.
Police believe Zerry is directly associated with the gang and are analyzing his device to uncover any information about the potential attack.
Disclaimer: The story, all names, characters, and incidents portrayed in this challenge are fictitious and any relevance to real-world events is completely coincidental.
Verify the Disk Image
The first question asks us to verify the disk image, and submit the sector count and MD5 hash corresponding to the disk image.
Q1) Verify the Disk Image. Submit SectorCount and MD5 (7 points)
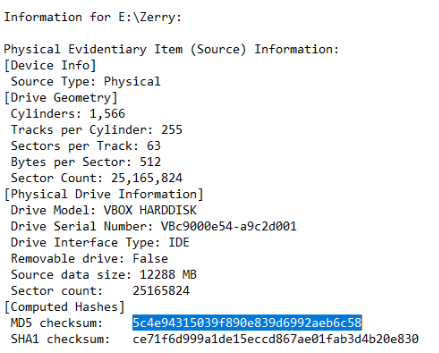
In most, if not all, cases E01 and EWF image files are accompanied by a secondary file in txt format which contains basic information pertaining to the disk image. If we therefore open the Zerry.E01.txt, we are presented with the information that is requested to answer question 1. The Sector Count is: 25165824 and the MD5 hash that is calculated over the disk image is: 5c4e94315039f890e839d6992aeb6c58
Finding the Decryption Key
The next question asks us to find the decryption key of the online messenger app that was used by Zerry.
Q2) What is the decryption key of the online messenger app used by Zerry? (7 points)
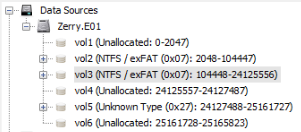
Once the image has been loaded, we expand the "Data Sources" tab as well as "Zerry.E01". Next, we are confronted with 6 volumes, of which 3 contain an underlying folder structure. Without looking into the specific folders, we can disregard volumes 1, 4, 5 and 6, since these are either Unallocated or of type Unknown. The remaining volumes are 2 and 3. Those familiar with Windows operating systems, will conclude that the main operating system is located in volume 3, since volume 2 starts at 0x2048, which for modern Windows systems, signals the bootloader section. Additionally, the size in bytes for volume 3 (24125556 - 104448) is significantly larger than that of volume 2: 104447 - 2048.
Applications and programs on Microsoft Windows use three main folders to store their data. The first folder is likely familiar to everyone reading this, the C:\Program Files folder, which should be used to store an application's read-only files. Applications that use persistent data that should be read and written during application runtime are actively discouraged from using the C:\Program Files folder. Instead, Microsoft offers to alternatives where applications should store this data. For files that the do not contain user-specific information related to the application, Microsoft advises to use C:\ProgramData. If the application handles user-specific information, then the application should use the users 'AppData' folder and often the subfolder 'Roaming' is used. This folder can be found in a users personal folder, like: C:\Users\*user*\AppData\Roaming.
Based on this information, let's first analyze the C:\Program Files folders. Remember that we are looking for an "online messenger app". In both of the Program Files folders, we don't find any clues. Note that applications might also install themselves directly in the User's AppData folder, specifically the Local subfolder. In that folder, one specific folder attracts the attention signal-desktop-updater. A Google search reveals that Signal Desktop is an online messenger application. Let's continue our analysis under the assumption that we have identified Signal Desktop to be the online messenger application in question. Note that Zerry's Downloads folder also contains an executable called signal-desktop-win-1.39.5.exe, further confirming our assumption.
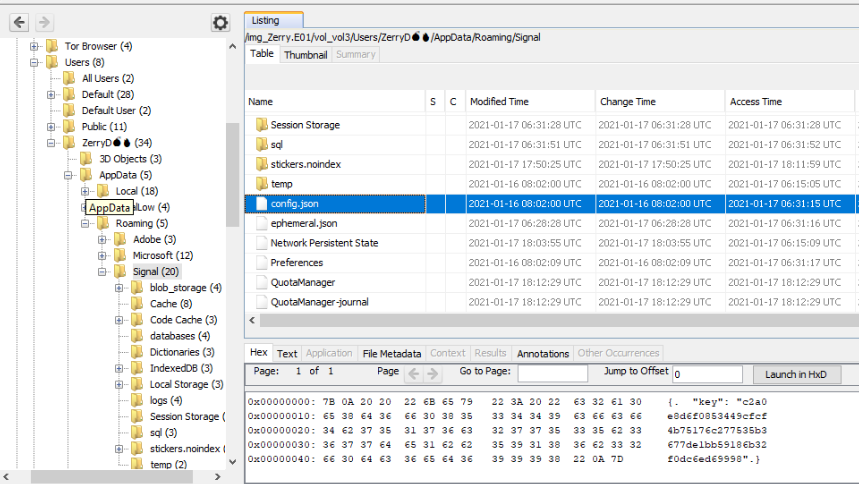
Now that we have found an online messaging application, we have two potential locations where the application data, and subsequently likely the encryption key will be stored. Since we are talking about a encryption key that should be unique for each user, the first location we will follow up will be Zerry's AppData folder. In C:\Users\ZerryD\AppData\Roaming we do find the Signal folder. Inside the main Signal folder, we identify multiple files, one of which is named config.json. If we open this file, we see that it contains a single line entry: {"key": "c2a0e8d6f0853449cfcf4b75176c277535b3677de1bb59186b32f0dc6ed69998"}. A quick Google search for the config.json file in combination with the keyword "Signal", brings us to this Reddit post, claiming suggesting that we have found the encryption key.
Discovering Zerry's profile information
Now that we have figured out the decryption key, we can look for additional details within the Signal folder pertaining to Zerry's profile name and registered phone number, to solve question 3.
Q3) What is the registered phone number and profile name of Zerry in the messenger application used? (7 points)
 Therefore, we extract this file from Autopsy and open it in the SQLite viewer that's included in the Tools folder on the desktop. When trying to open the database, we are met with a prompt for a password.
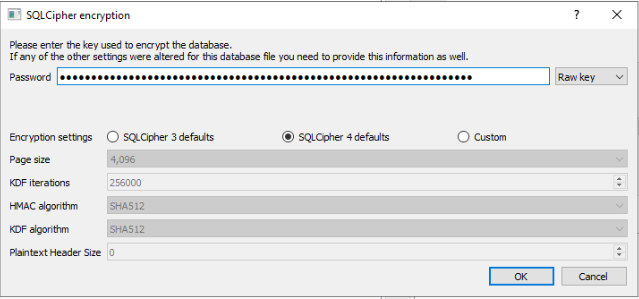
To be able to decrypt the contents of the database, we will need the encryption key we have discovered earlier. In the menu, set the authentication method from Password to Raw Key. Notice that it prompts
to add 0x in front of the key, meaning that the actual decryption key is 0xc2a0e8d6f0853449cfcf4b75176c277535b3677de1bb59186b32f0dc6ed69998.
Therefore, we extract this file from Autopsy and open it in the SQLite viewer that's included in the Tools folder on the desktop. When trying to open the database, we are met with a prompt for a password.
To be able to decrypt the contents of the database, we will need the encryption key we have discovered earlier. In the menu, set the authentication method from Password to Raw Key. Notice that it prompts
to add 0x in front of the key, meaning that the actual decryption key is 0xc2a0e8d6f0853449cfcf4b75176c277535b3677de1bb59186b32f0dc6ed69998.
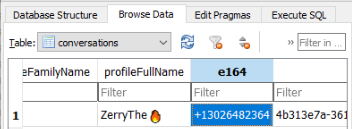
Now that we have obtained access to the database, we can browse through the tables. Specifically in the conversations table, we find a single entry containing both the profile name and the telephone number that were used by Zerry: ZerryThe and +13026482364.
Looking for Zerry's email address
Q4) What is the email id found in the chat? (7 points)
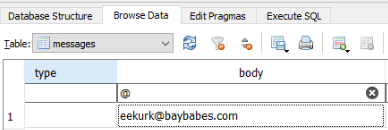
Identifying the email attachment
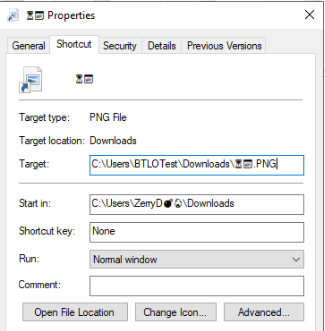
Q5) What is the filename(including extension) that is received as an attachment via email? (7 points)
Attack date and time
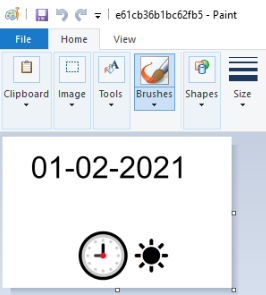
Q6) What is the Date and Time of the planned attack? (7 points)
Attack GPS Location
Now that we have obtained most of the details pertaining to the attack, one main challenge remains: figuring out where the attack will take place:
Q7) What is the GPS location of the blast? The format is the same as found in the evidence . [Hint: Encode(XX Degrees,XX Minutes, XX Seconds)] (8 points)
Hint: It is possible this information was stored in a Sticky Note. Find this in /Users/Zerry/AppData/Local/Packages and export it. Open the plum.sqlite database file in the /LocalState/ directory using SQLiteDatabaseBrowser. Find which table the notes are stored in. We can work out how to decrypt the encoded result by checking recent sites visited via Tor in Autopsy by looking at /Tor Browser/Browser/TorBrowser/Data/Browser/proile.default/places.sqlite.
Building upon these hints, we browse to C:\Users\ZerryD\AppData\Local\Packages\Microsoft\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqlite. Next we extract the database, open it in the SQLite browser and notice that it contains one entry for the table "Note" with text: 40 qrterrf 45 zvahgrf 28.6776 frpbaqf A, 73 qrterrf 59 zvahgrf 7.944. Downloading the places.sqlite database from the location C:\Tor Browser\Browser\TorBrowser\Data\Browser\profile.default and analyzing its entries, we notice that the website "rot13.com" was visited. Those familiar know it also as the Caesars Cipher, which substitues a letter with the 13th letter after it. As such, we can decode the value we found on the sticky note. Decoding it with ROT13 using Cyberchef gets us the result: "40 degrees 45 minutes 28.6776 seconds N, 73 degrees 59 minutes 7.994 seconds W".
