Introduction
Today we will be walking through one of the Blue Team Labs Online Investigations: SOC Alpha 3. The Investigation is
rated as "Hard" and will earn you 100 points. To earn full points, you have to answer 17 questions in regard to
the following scenario:
Just like SOC ALPHA 2 lab, you are provided with the more alerts triggered on the ingested logs in ELK. Show your hunting skills to answer the questions for each alert.
Note: While submitting answers, ignore the escape characters and double quotes if any
Example:
If you found an answer: “C:\\Windows\\System32\\cmd.exe”, submit the answer as: C:\Windows\System32\cmd.exe
Additionally, within the Lab we find a README that supplies some information on the hunting scenario's for this case:
H1 - Compression of collected data (T1560)
H2 - New Run Key to suspicious folder
H3 - EventLog Cleared
H4 - New Windows Firewall rule added
H5 - Suspicious File Download
H6 - DarkSide Ransomware Pattern Detected
H7 - CoinMiner Activity detected
H8 - Multiple services stop
Q1) Compression Program
Q1) What program is used for compression? (5 points)
When we load into Kibana, we see that there are 4 index patterns at our disposal focussing on PowerShell, Security, Sysmon and System events that
were gathered from the system. Since we are looking for the execution of a program to compress a file, we will use the sysmon event logs.
Specifically, we will look for events with Event ID 11, which signals the creation of a file. Since a large amount of files are returned that were
created by the MsMpEng process, we will go ahead and filter these out:
Event_System_EventID: 11 and not Event_EventData_Image: "C:\\Program Files\\Windows Defender\\MsMpEng.exe
This leaves us with 105 hits. As we are focussing on a program that can be used for compression, we can relatively quickly disregard most entries, until
we stumble upon
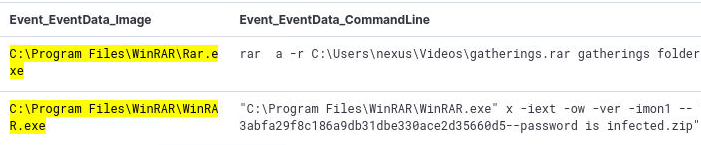
C:\Program Files\WinRAR\WinRAR.exe. We see that it is used to compress a file in the Downloads directory
that has a hash as its name. Additionally, two log entries further, we see that an executable with the same hash value is creating an README.47bf44bd.TXT.
A quick Google on the hash shows it is related to a ransomware campaign. So we can assume that WinRAR is used for compression.
However, the entry that we have identified, is used to decompress/unzip a file. As no other applicable files are found, I focus on EventID 1, which
corresponds to process creation events. Here, I apply a filter to search for WinRAR only:
Event_EventData_Image: *WinRAR*
Only 2 processes remain, of which one is actually a compression operation, confirming that the program that is used is
C:\Program Files\WinRAR\WinRAR.exe
![q1_answer]()
Q2) Compressed File Name
Q2) What is the name of the compressed file? (5 points)
Now that we have identified the program that is used, we can closely examine the command line to figure out what the name of the compressed file is.
We see that the files/folders "gatherings" and "folder" were compressed into
gatherings.rar.
![q2_answer]()
Q3) Registry File Add
Q3) What is the name of the file that has been added to the registry? (6 points)
For Windows Registry events, we remain within the winevent-sysmon view and we can look for EventID 13, which contains Registry Events where a value is set.
We identify 37 unique events and focus on events that have a RuleName which corresponds to a MITRE Attack Flow technique. Only three techniques are documented.
One which refers to DOM Hijacking (T1122), one which refers to the creation or modification of system processes(T1031/T1050) and one which refers to the
creation of a run key (T1060).
All events with rule T1122 don't contain a value that resembles a file, so these are left out of scope. All events with rule T1122 point to DLLs however,
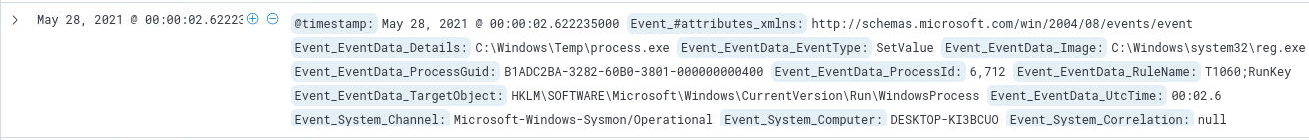
these are related to Windows Defender and appear to be legitimate. The sole event for T1060 points to a file in the Windows Temp directory, namely:
C:\Windows\Temp\process.exe. Additionally, that file is added to a generic, and somewhat suspicious sounding, object
WindowsProcess
![q3_answer]()
Q4) Registry Value
Q4) What is the RegValue? (6 points)
As identified in question 3, the file
C:\Windows\Temp\process.exe is added to the RegValue of
WindowsProcess
![q4_answer]()
Q5) Log Clearing Timestamp
Q5) What is the timestamp when the logs are cleared? (6 points)
If we have a look at the MITRE Attack Flow, we learn that clearing the event logs is a subcategory of indicator removal and known as technique T1070.001.
Additionally, the
webpage logs example commands to identify log clearing. If we use the
keyword "wevutil" and search for it's usage as an Event_EventData_Image within the winevent-sysmon logs, we identify two commands where the security
logs got cleared. However, the timestamps do not seem to be correct answers. So we have to continue our hunt.
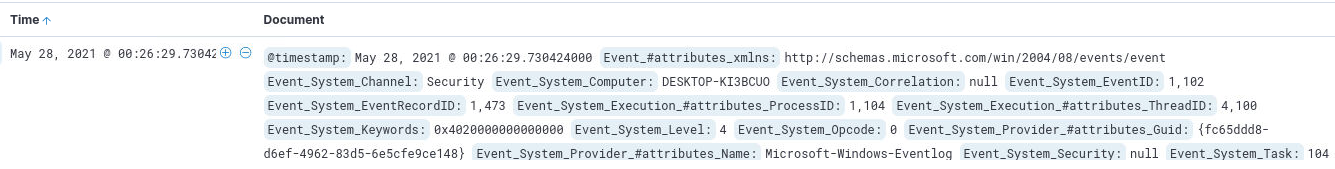
We also
learn
that we can identify clearing of the audit logs by searching for Event ID 1102 in the Security log. So we change our view in Kibana to the security log
and apply that filter, which returns exactly one result. The log was cleared at
2021-05-28T00:26:29.
![q5_answer]()
Q6) Log Source Confirmation
Q6) What is the logsource from which you confirmed this event and what is the fieldname and value in the log? (6 points)
As discussed whilst answering question 5, we had to utilize the
winevent-security log and search for
Event_System_EventID: 1102 to confirm the log clearing event.
![q6_answer]()
Q7) Firewall rule addition
Q7) What is the program used for adding the firewall rule? (6 points)
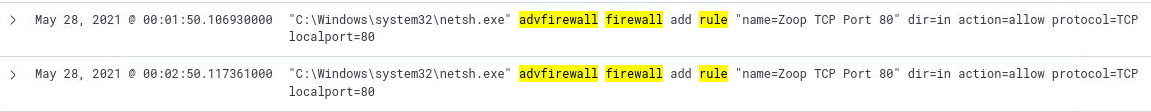
We can search for Firewall events using the winevent-sysmon log and searching for process creation events. The programs that I am familiar with, all require
you to use some variant of the word "firewall" or "rule" to add firewall rules. So I will add a specific query which includes the usage of these two words
in the CommandLine and we identify only two commands that apply. We see that to add firewall rules, the program
netsh.exe was used.
![q7_answer]()
Q8) Firewall Rule Name
Q8) What is the rulename? (6 points)
As identified in question 7, the rule that was added was named:
Zoop TCP Port 80
![q8_answer]()
Q9) Malware Downloader
Q9) What is the program used for downloading the suspicious file? (6 points)
Once again, we rely upon EventID 1 in the sysmon log files and search for download actions. I worked with the assumption that the download took place
over the internet, and as such added both "http" and "https" to my search query using:
Event_EventData_CommandLine: *http*.
Only one event is identified, which shows us that
bitsadmin.exe was used to download a file from pastebin and store it on
the local system as a powershell file. Bitsadmin is a
living-off-the-land binary
which can be used to download files from remote sources.
![q9_answer]()
Q10) Download URL
Q10) What is the URL from which the file is downloaded? (6 points)
As identified in question 9, the suspicious file is downloaded from the url
https://pastebin.com/raw/AGdtReXJ0
![q10_answer]()
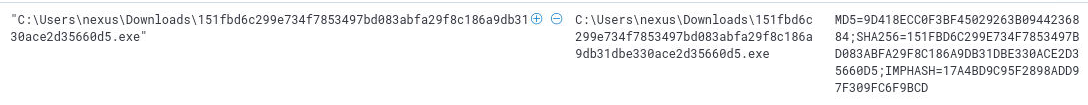
Q11) Darkside Ransomware
Q11) Hunt for the darkside ransomware sample and what is the MD5 hash of the sample? (6 points)
Whilst solving question 1, I already had stumbled upon the DarkSide ransomware sample due to the usage of the SHA256 hash as the name for the executable.
This stood out to me and has now allowed me to search for the specific hash in the winevent-sysmon events specifically focussing on EventID 1 as sysmon
automatically includes MD5, SHA256 and IMPHASH hashes in each log entry. As such we identify that the DarkSide ransomware sample has MD5 hash:
9D418ECC0F3BF45029263B0944236884
![q11_answer]()
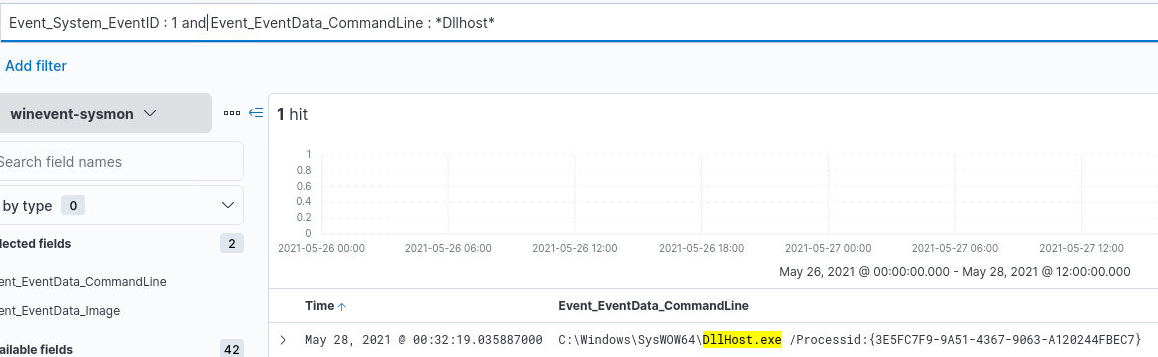
Q12) Command execution
Q12) The alert is triggered using the processid flag of DllHost.exe, find out the full command associated with it (6 points)
Once again, we remain with the sysmon event logs, focussing on process creation (EventID 1) and search for all command lines containing "DllHost". We find
only one such event whose full command line is:
C:\Windows\SysWOW64\DllHost.exe /Processid:{3E5FC7F9-9A51-4367-9063-A120244FBEC7}
![q12_answer]()
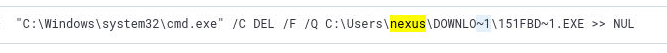
Q13) Malware delection command
Q13) There is an event to delete the malware from the system. Can you find the full command? (6 points)
We already know, that based on the results for question 11, searching for the specific SHA256 hash won't result in any logs that point to removal of
the malware. However, as we also don't find any indicators that the malware is removed, we focus on all commands that were performed on the folder
in which the malware was located:
Event_System_EventID : 1 and Event_EventData_CommandLine : *Downloads*. To my surprise,
no other log entries are found that indicator removal. So I applied the same filter but then using "nexus" as the CommandLine filter. Here, we discover
an event that points to malware removal. The command used, uses Windows' 8.3 naming rules for creating short file name aliases as documented
here.
![q13_answer]()
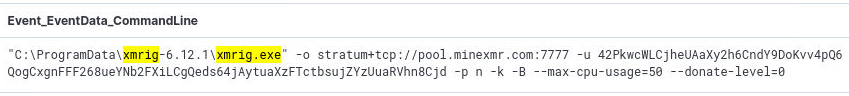
Q14) Mining Server
Q14) What is the username of the mining server used? (6 points)
Whilst answering multiple of the previous questions, I mentioned that I used EventID: 1 in the winevent-sysmon logs to look for process creation events.
Whilst doing this, and analyzing the events, I already stumbled upon the execution of the executable
xmrig.exe. I know from
experience that this is an cryptominer that is used for legitimate and illegitimate purposes. Searching for all process creation events involving xmrig,
a total of 5 events are found. Only one however, starts the miner and includes the username:
42PkwcWLCjheUAaXy2h6CndY9DoKvv4pQ6QogCxgnFFF268ueYNb2FXiLCgQeds64jAytuaXzFTctbsujZYzUuaRVhn8Cjd
![q14_answer]()
Q15) Mining version
Q15) What is the version of the miner? (6 points)
In the command line of the xmrig miner, we see that the exectuable is located in
C:\ProgramData\xmrig-6.12.1\xmrig.exe,
as such we can assume that 6.12.1 is the version of the miner.
![q15_answer]()
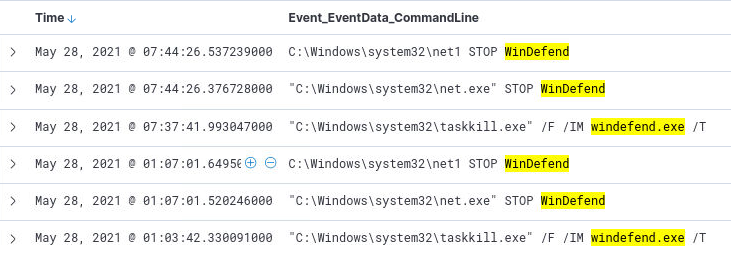
Q16) Stopping Windows Defender
Q16) What is the full command attempted to stop the windows defender? (6 points)
A quick Google search reveals that the Microsoft Defender Antivirus Service is called
WinDefend.
Using our reliable Event ID 1 within the sysmon event logs with the filter
Event_EventData_CommandLine: *WinDefend* we identify
multiple commands aiming to stop the service such as:
C:\Windows\system32\net1 STOP WinDefend and
"C:\Windows\system32\net.exe" STOP WinDefend
![q16_answer]()
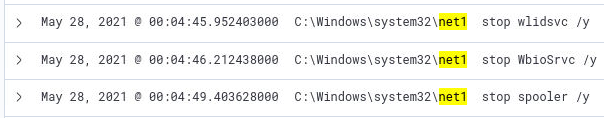
Q17) Targeted Services
Q17) From cmd.exe, the attacker tried to stop 3 more services with a bypass prompt flag. What are the services in alphabetical order? (6 points)
Since we have identified, by answering question 16, that
net.exe/net1 is used to stop services, we focus on
all commands containing either
"net1 or
"net.exe. Note that filtering for
net will show a lot of non-related events as well, therefore we use an OR filter. By doing so, we remain with
22 logs and see that the
/y switch is used for only 3 services. Except for
this
mention I have not found a reliable source indicating that the
/y switch is used for bypassing prompts.
However, since it specifically suits our scenario, my assumption is that we can rely on the information on the aforementioned webpage,
and we have identified which three services were stopped by the attacker using the bypass prompt flag.
![q17_answer]()