Introduction
Today we will be walking through one of the Blue Team Labs Online Investigations: The Key. The Investigation is
rated as "Hard" and will earn you 100 points. To earn full points, you have to answer 18 questions in regard to
the following scenario:
Peter, a programmer by profession, was always fascinated by Superhero movies from his childhood. He started a secret project at work without informing his Boss. Peter stored all the project files in his cloud account. His Boss came to know about Peter's secret project and asked the security team to investigate Peter's laptop. But, here comes the real headache, Peter's secret drive is encrypted!
Investigate the Disk, Help Boss in finding the Decryption Key and the Cloud Credentials of Peter.
Note: This investigation involves both Technical and Content Analysis. We suggest players immerse themselves in the scenario.
Timezone information
Q1) What is the TimeZone of Peter's Machine? [Hint: Find The Registry Key] (3 points)
The Windows Registry contains a wealth of information in regards to the operating system and numerous of its settings and locales. One of the datapoints
stored in the registry is information on the timezone that was set on the computer in question. To extract this value from the registry, we first have
to download the SYSTEM hive from the forensic image. Using FTK Imager, load the
E01 image. The SYSTEM hive by default is
located in
C:\Windows\System32\Config. Download the hive and proceed to open the Forensic Registry EDitor (FRED) supplied
as a tool on the host. Next load the hive, and browse to the location
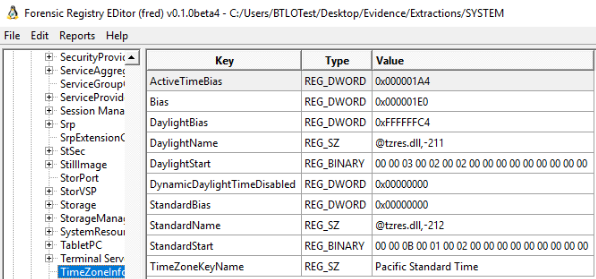
ControlSet001\Control\TimeZoneInformation.
Identify the key
TimeZoneKeyName which contains the value value
Pacific Standard Time.
![q1_answer]()
Superhero Stories
Q2) Superhero stories were introduced to Peter at his school. What is the name of the Peter's School? (10 points)
The attentive reader will focus their attention on "Peter's School" rather than on the "Superhero stories" part of the question. Those who have previously
setup a local-only account on a Windows system, might be familiar with
security questions.
These security questions can be used to recover a lost account or a forgotten password. Windows requires users to submit at least three security questions with
corresponding answers. Additionally, Windows only allows a default set of questions, one of which asks for "What was the name of the first school you attended".
There are two ways in which the answers to the security questions can be retrieved. For both methods, we will need to access the SAM file. The SAM file is
a database file that stores user account details and is located at
C:\Windows\system32\config\SAM.
The first method will use the NirLauncher. This is a utility-packed toolsuite that can be used in a whole host of scenarios and cases. Familiarize yourself
with the list of utilities and description as can be found on the
NirLauncher website. You
will identify a specific tool called
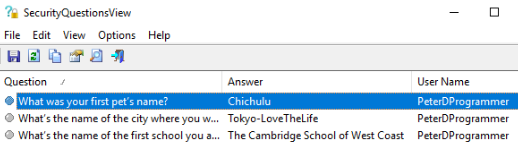
SecurityQuestionsView which provides an interface to view the security questions and
their answers stored in the registry by the Windows 10 operating system. Loading the SAM file into the application, will show us that Peter went to
The Cambridge School of West Coast.
The second method will utilize the previously used FRED. Load the SAM database and go to Domains -> Account -> Users -> Names -> PeterDProgrammer ->
ResetData Key. Then decode the data from hex and discover the school Peter used to go to.
![q2_answer]()
Favourite Quote
Q3) What is Peter's Favourite Quote? (10 points)
As opposed to question 2, this question doesn't leave us any clues and a hunt for something tangible that could lead the way to the answer begins.
In previous challenges that I have solved, sticky notes were used for similar questions. However, the sticky notes did not contain anything valuable.
After some painstaking time, I thought about the background image since people tend to use motivational or inspirational backgrounds. According to
multiple
sources,
Windows stores the background image in the location
C:\Users\PeterDProgrammer\AppData\Roaming\Microsoft\Windows\Themes\CachedFiles.
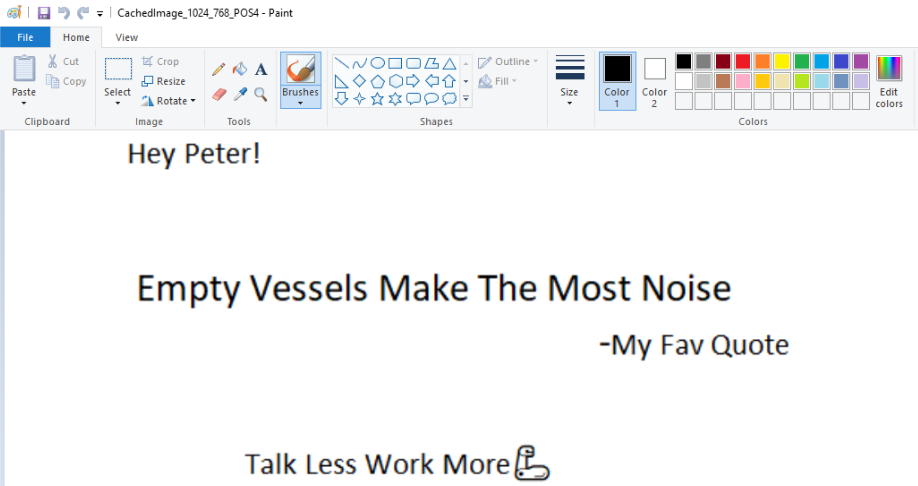
As expected in the CachedFiles we discover an image and exporting it and opening it in an image viewer (e.g. Paint) will supply us with the quote:
Empty Vessels Make The Most Noise.
![q3_answer]()
Computer Name and IP info
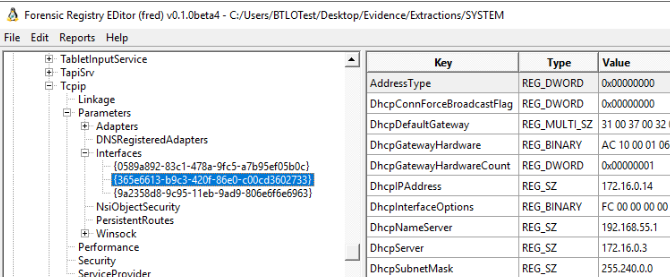
Q4) What is Peter's IP Address and Computer Name? (5 points)
As discussed during question 1, the registry stores a lot of information on the operating system. We once again rely upon the SYSTEM hive to supply
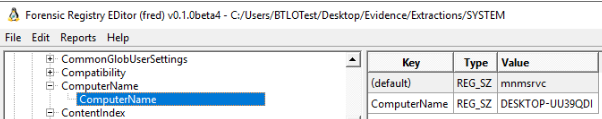
us with the two answers for this question. Using FRED, we can locate the computername under
ControlSet001\Control\ComputerName\ComputerName
and the IP address can be found be going through each interfaces under
ControlSet001\Services\Tcpip\Parameters\Interfaces\{365e6613-b9c3-420f-86e0-c00cd3602733}
![q4_answer0]()
![q4_answer1]()
Programming Language
Q5) What is the name of the programming language peter is learning? (2 points)
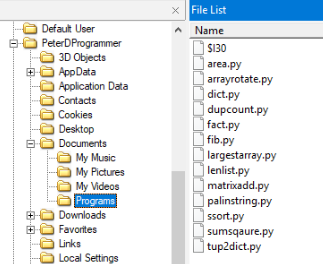
By browsing through the local folders in Peter's user folder, we identify the executable
python-3.9.4-amd64.exe in the
Downloads folder. Additionally, in the Documents folder, a subfolder called "Programs" exists which hosts multiple python files. Furthermore, we
identify in
C:\Users\PeterDProgrammer\AppData\Roaming that Peter uses Notepad++. Notepad++ keeps a backup folder where
sessions are stored. Within this folder, we identify one Notepad++ session which we can extract and view with a text editor. This session contains the
text:
starting my python journey. As such, we can conclude that Peter is learning the Python programming language.
![q5_answer]()
Peter's Day Plan
Q6) According to Peter's Day Plan, Which task is "In Progress"? (5 points)
Based on question 5, we also identified a reference to creating a dayplan in the Notepad++ backup. However, no other notes can be found within Notepad++.
Simultaneously we see though, the Peter makes use of Sublime Text 3, which, much like Notepad++, is a text editor as well. So, the next logical step was
to look at the stored Sublime session(s) in
C:\Users\PeterDProgrammer\AppData\Roaming\Sublime Text 3\Local\. Within this
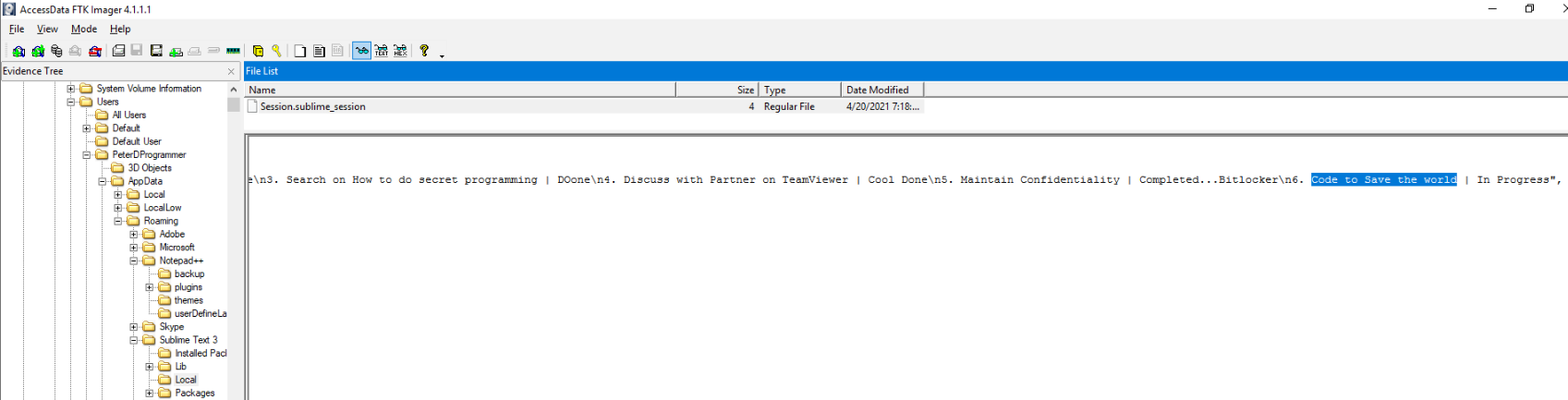
folder, we identify the existence of the file:
Session.sublime_session. This file contains the tasks in Peter's Day Plan,
of which
Code to Save the world is still in progress.
![q6_answer]()
TeamViewer Partner information
Q7) Peter connected with his partner using TeamViewer. What is the Peter partner's Teamviewer ID and Display Name? (5 points)
The TeamViewer application stores incoming connections in a file called
Connections_incoming.txt, most often located in
the installation directory of TeamViewer at
C:\Program Files\TeamViewer. The actual log message ends with 2 fields if
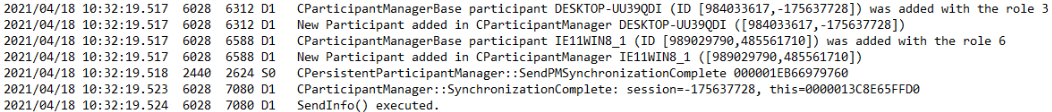
the log message starts with
New Participant added. The first field represents the partner's TeamViewer ID and the
second field contains the DisplayName.
Instead of using the
Connections_incoming.txt file, it is also possible to check the
TeamViewer15_Logfile
located in the same folder and search for log entries containing
New Participant added messages. The corresponding ID and DisplayName are:
989029790, IE11WIN8_1
![q7_answer]()
Peter's TeamViewer Information
Q8) What is Peter's TeamViewer ID and Display Name? (5 points)
Since we already know the computername of Peter's computer, we can search for that value in the same logs we used to answer question 7.
With this information we discover that Peter's TeamViewer ID is:
984033617
![q8_answer]()
Password Manager
Q9) What is the Password Manager used by Peter? (5 points)
The first step to answering this question, is identifying where said Password Manager is installed. In order, I investigated the
Program Files
and
Program Files (x86) folders, alongside Peter's
AppData folder. When no indications of
Password Managers were found, I looked into the Prefetch files to identify if a Password Manager was executed and if that was done from outside one of
the previously mentioned locations. However no indications could be identified. Next, I decided to look for browser/internet-based Password Managers.
Working with the assumption that since no additional browsers are installed, the default browser on Windows, Edge, was used, I retrieved the browsing history.
It's history location file is stored at
C:\Users\PeterDProgrammer\AppData\Local\Microsoft\Edge\User Data\Default\History.sqlite.
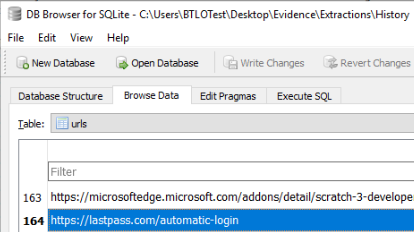
Extracting this SQLite database and opening it in DB Browser for SQLite, we browse to the urls table and find an entry for
https://lastpass.com/automatic-login.
With this trivial piece of information in hand, we can conclude that Peter uses LastPass as a password manager.
![q9_answer]()
VPN Service
Q10) What is the VPN service used by Peter? (5 points)
Whilst searching for the Password Manager software on the local system as mentioned whilst answering question 9, I kept an eye out for VPN software
installed in any of the same researched folders or logged in the Prefetch files. Once again, no local installation of a VPN service could be identified.
Therefore, we stay with our scope focussing on Edge. Since no history could be found, I decided to also peruse the WebCacheV01.dat file, stored in
C:\Users\PeterDProgrammer\AppData\Local\Microsoft\Windows\WebCache which can be analyzed with the BrowsingHistoryView tool
provided by NirSoft. No such luck however, and that's when I got reminded of Browser Extensions. These extensions are stored on the local system as well
in the folder
C:\Users\PeterDProgrammer\AppData\Local\Microsoft\Edge\User Data\Default\Extensions. The folder names are all
obfuscated and the quickest way to retrieve information on the installed extensions is by going into the
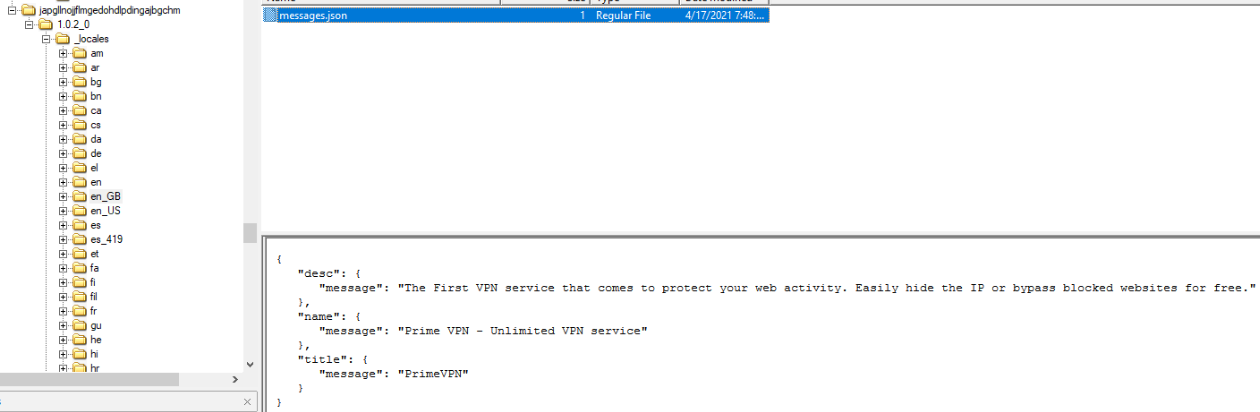
_locales folder and
opening the
messages.json file. By doing this, we discover that Prime VPN is used by Peter.
![q10_answer]()
Peter's Secret Project
Q11) What is the name of the Peter's 'Secret Project'? (5 points)
Figuring out the answer to this question proofed to be quite the challenge and you will need multiple puzzle pieces to solve it. First of all, refer
back to question 10, where we used the BrowsingHistoryView tool to analyze the WebCacheV01.dat file. Attentive people will have noticed that there were
references to files stored on the
D:\ drive as well as two files stored in Peter's Documents folder referring to BitLocker.
![q11_answer]()
Additionally, from the challenge description we know that there is a secret drive that is encrypted. I was under the assumption that the secret drive
was attached in the E01 image as partition 4. However, I also noticed that the host OS has drives D, E, F and G which in other investigations has not
been the case. That's when I dived into the tools that are to our disposal and noticed that I hadn't used Arsenal Image Mounter so far, and in general
never used that piece of software before. I
read up on it, and then figured out
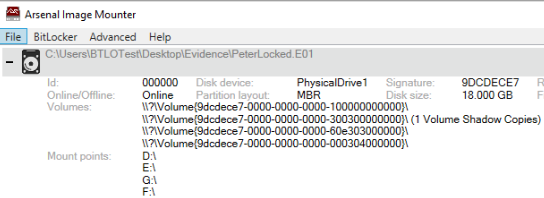
that you can mount images to your location system. If we mount the disk image using the online mode, we see that all volumes are already mounted to
the four previous drives (D, E, F and G) that we had noticed earlier. Additionally, we identify that the second volume has a volume shadow copy.
![q11_answer]()
A
Volume Shadow Copy are snapshots
captured by the operating system and store copies of files and volumes at specific points in time, enabling users to restore previous versions of
files or entire volumes. As such, playing a vital role in covering data that we need to solve this and likely the next questions. We can assume that
the volume containing the volume shadow copy is likely mounted to the
E: drive, since the D and G drive are empty and F
is an encrypted volume.
We can use the command
vssadmin list shadows /for=E: to obtain a list of shadow copies for the
E:
drive drive. One copy is identified, which we would be able to restore using the make link command in Windows:
mklink /D C:\vssrestore \\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1\.
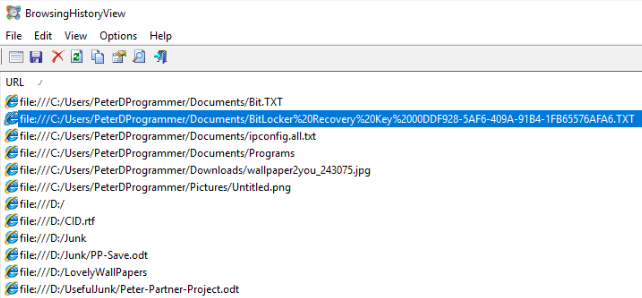
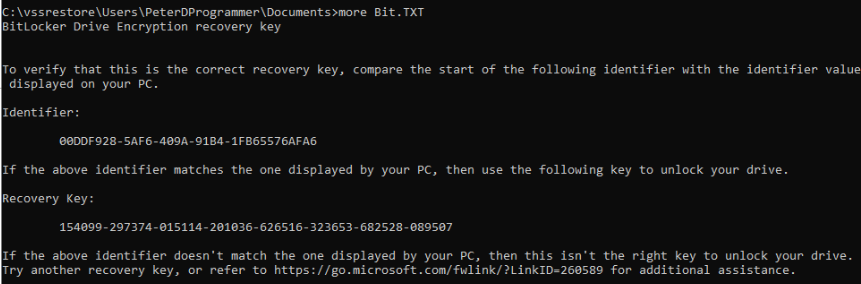
Since we executed these commands in an administrator CMD session, we will use the terminal to dive into the contents, with the focus on the Documents folder.
In said folder, we identify the
Bit.TXT file, which holds the Bitlocker Recovery Key.
![q11_answer]()
We can use that key, to unlock BitLocker encrypted drive
F: drive, by selecting to use the BitLocker Recovery Key. With the
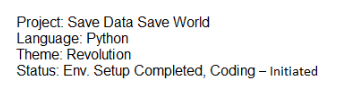
access we have obtained, we can browse through the drive and identify Peter's project to be "Save Data Save World".
![q12_answer]()
Peter's Project Theme
Q12) According to the Peter's documentation, What is the theme of the project? (5 points)
We can use the same document we used to answer question 11 and discover that the theme is "Revolution"
![q12_answer]()
Cloud Credentials
Q13) What are Peter's Cloud Credentials? (10 points)
Inside the decrypted
F: drive, we identify a file called CID (Client identifying Information) which initially
seemed to only contain his username, but if we use "select all", we identify white-colored text containing his password.
![q13_answer]()
Discord Malware Name
Q14) Peter accessed some files from a remote machine using a file transfer service. What is the login name and IP address of the remote machine? (5 points)
There are multiple file transfer services that work on Windows, however, from our research on both the VPN service and Password Manager, we should remember that we
saw that WinSCP was present in the
C:\Program Files (x86) folder. WinSCP is the Windows-based secure copy program that can be used
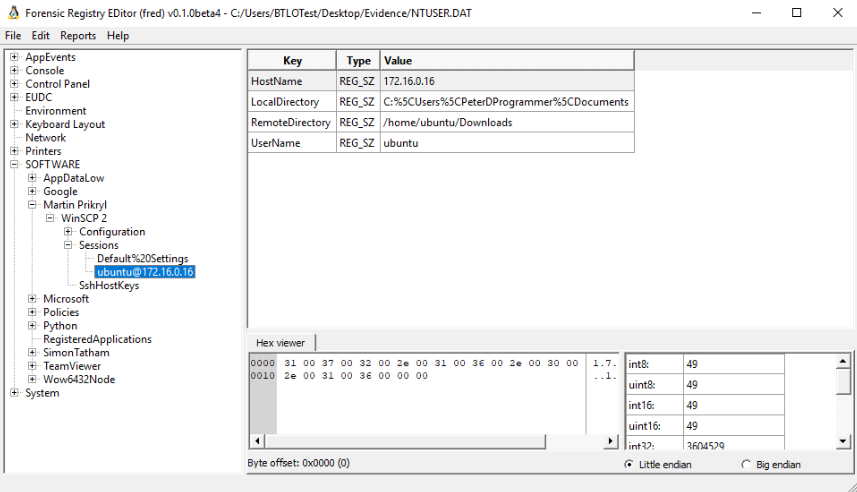
as a network-based file transfer service. WinSCP stores some configuration and session details in the Windows registry for each user. Therefore, we acquire Peter's
NTUSER.dat> file and examine it with FRED. Since it's a software package, we can search under the SOFTWARE key. Note that WinSCP
is developed by Martin Prikryl, which is the main key the WinSCP configuration and session data is stored under. We identify a Sessions key which contains
one object containing the username and hostname that were connected to:
ubuntu@172.16.0.16
![q14_answer]()
BitLocker Recovery Key
Q15) What is the Bitlocker Recovery Key? (10 points)
In order to answer this question, refer back to the writeup for question 11. Here, we had already identified the BitLocker Recovery Key.
![q15_answer]()
BitLocker Password
Q16) What is the Bitlocker Password? [Hint: Question 2] (10 points)
Figuring out the BitLocker Password required some brute-forcing but we were given a valuable hint to refer back to the answer for question 2.
In that light, I figured it must be either one specific answer to one of the three security questions or a combination of them. Eventually, the latter
appeared to be true with the password being a combination of the first and second question:
ChichulaTokyo-LoveTheLife
![q16_answer]()