Challenge Writeup
When launching the application you will see two instructions:
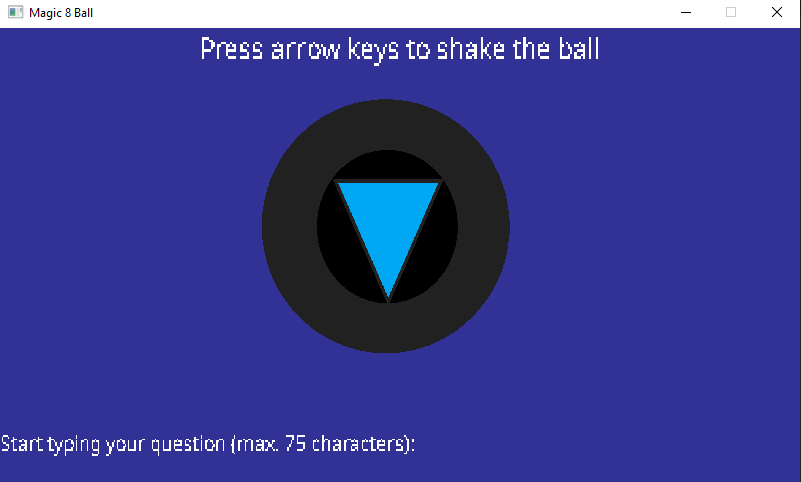
1. Press arrow keys to shake the ball.
2. Start typing your question (max. 75 characters)If we glance over the imports table, we identify that a substantial amount of functions of the SDL2 libary are imporated, as shown in the screenshot below. The SDL2 library supports the Simple DirectMedia Layer.
Simple DirectMedia Layer is a cross-platform development library designed to provide low level access to audio, keyboard, mouse, joystick, and graphics hardware via OpenGL/Direct3D/Metal/Vulkan. It is used by video playback software, emulators, and popular games including Valve's award winning catalog and many Humble Bundle games. The main entrypoint of the application is the WinMain function which calls a single function sub_403690.
Analyzing this function, we can identify that it will check if any command line arguments are given, handle those and will then call
SDL_SetMainReady before calling sub_4027A0. Based on the documentation, we
can assume that the code so far has initialized the environment, and we can resume our analysis by diving into the last function that is called.
The main entrypoint of the application is the WinMain function which calls a single function sub_403690.
Analyzing this function, we can identify that it will check if any command line arguments are given, handle those and will then call
SDL_SetMainReady before calling sub_4027A0. Based on the documentation, we
can assume that the code so far has initialized the environment, and we can resume our analysis by diving into the last function that is called.
The first three blocks until 0x40281d seem to do more initialization processes such as loading strings, fonts, and setting buffers. The application then calls sub_402090 on which we will now focus our attention. We identify more SDL2 function calls responsible for creating images, a window and a renderer. Furthermore, we identify that a 4x4 hex characters get loaded into a register 6D6D69676C662065702067613F736C. When we decode this hex string, we find out it resolves to gimme flag pls?. We assume that this string that this string might be of importance later on. Note how the string is stored in a dowrd pointer starting at edi+5Ch. Furthermore, a little down we identify the strings that are visible in the program and serve as instructions on how to operate the program.
Since we know that SDL2 is used for keyboard events, I read up on the documentary and discovered that the function SDL_PollEvents is used to listen for keyboard events. This function is only used twice within the same function: sub_401E50, which is closely located in relation to the previous functions we have analysed. As such, the assumption is made that the call at Magic8Ball+2888 contains the first part of the logic to get the flag.
As it was not immediately clear what the usage of this function was, a couple of breakpoints were set on the multiple if-statements within this function. Because the SDL_PollEvents function will handle _all_ events, it should be possible to deduce when the user-input will be handled. After some trial-and-error, it appeared that setting a breakpoint on Magic8Ball+26B9, before execution, then using the arrow keys and entering the question and pressing "ENTER" would result in the execution flow ending up here. From hereonwards, we see a nested if structure, which eventually result in a call to strncmp.
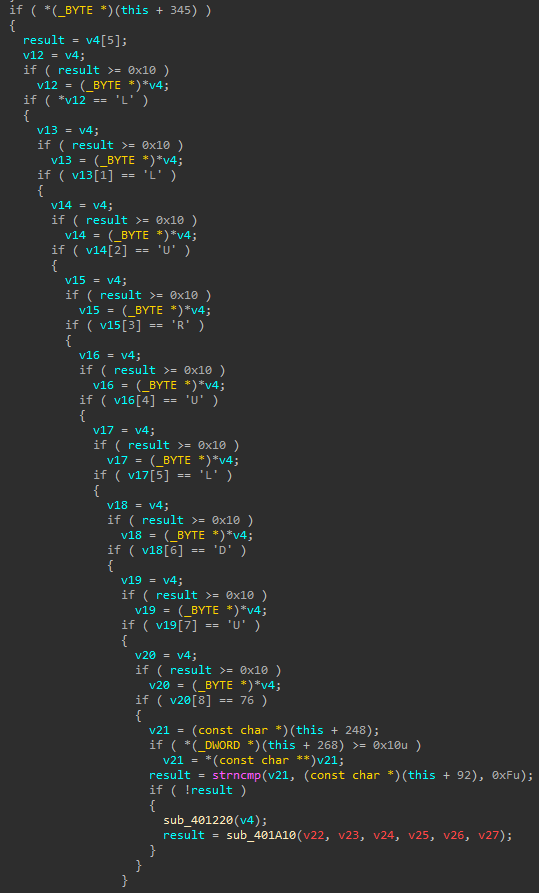
For every if-statement, it is checked if the value in [ecx+x] where x is an incrementing number starting at 0, is equal to a certain hex-value. Checking all the if-statements it became obvious that there were only 4 unique hex-values that were considered 'valid' input. These values corresponded to the letters L, R, U, D, which correspond to the arrow keys for "left, right, up & down". With this new insight we could reverse what the expected pattern is: LLURULDUL. If this pattern was hit, the user would then need to input a "question". Following execution flow, we see that the user's input is subsequently compared using strncmp against the earlier identified hardcoded string "gimme flag pls?" stored in a pointer to edi+5Ch.
Thus, by inputting the arrow key combination "LLURULDUL" and asking the question "gimme flag pls?" we obtain the flag for this challenge: U_cRackeD_th1$_maG1cBaLL_!!_@flare-on.com. And with that, we have completed the third Flare-On challenge!

